Techniques for assessing privacy and data protection in software systems
This post is a summary of “A Systematic Mapping Study on Software Quality Control Techniques for Assessing Privacy in Information Systems”, which is available here.
The major result of this systematic mapping study is the identification and classification of existing SQC techniques that detect privacy-related anomalies during the development process of software-based information systems (IS). For researchers, we provide an overview of research efforts on the different types and subtypes of SQC techniques used throughout the software development process, highlighting the targeted privacy properties, analyzing some research trends, and identifying main research institutions and publication venues. For both researchers and practitioners, we show the specific targeted software artefacts to which the SQC techniques can be applied, as well as the conditions or criteria used to detect anomalies.
The reported state-of-the-art techniques fall into one of three types of SQC techniques. Static analysis techniques aim at assessing and finding anomalies in different representations or models of the system. Dynamic analysis techniques examine the real behaviour of the system at runtime. Finally, hybrid approaches combine static and dynamic techniques. Table 1 below shows some subtypes into which the different techniques were also classified.
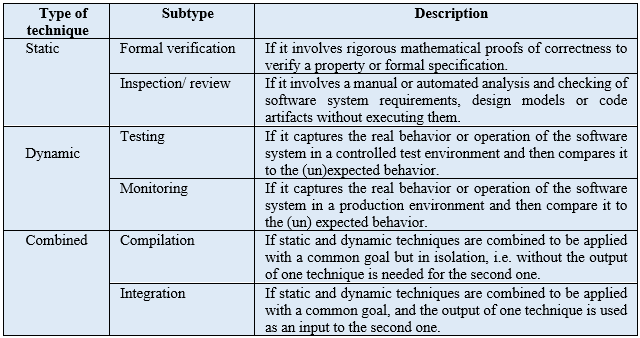
Fig. 1 shows the distribution of the techniques reported, which have been published throughout the last 20 years. The number of publications has increased continuously from 2010. This has increased even more in the last five years (from 2015 to 2019), which concentrates more than two thirds of the total number of published articles (46 out of 64).
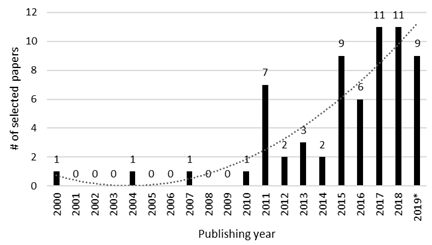
Fig. 2 provides a summary of the types and subtypes of SQC techniques that have been reported in a set of 64 papers, according to the categories presented in Table 1. We can see that the research efforts for finding privacy-related anomalies in software-based IS are led by static techniques (53%), followed by dynamic techniques (30%), and combined techniques (17%). Note that when a paper reports a combined technique, it necessarily made up of two individual SQC techniques working together: one static technique and one dynamic technique. As a result, the papers studied report a total of 75 different instances of static and dynamic techniques for assessing software-based IS in order to detect privacy-related anomalies: 34 falling into the static technique category and 19 into the dynamic technique (see Fig. 2a), plus 11 static techniques and 11 dynamic techniques which were combined to be applied with a common goal (see Fig. 2b).
Please read our full paper which provides more details on SQC techniques reported, including the different criteria or conditions that circumscribe when privacy is preserved or violated, the specific software artefact to which an SQC technique is applied, as well as their level of maturity.
About Danny Guamán
Ph.D. student at Technical University of Madrid (Spain). Auxiliary professor at Escuela Politécnica Nacional (Ecuador). Current interests: Privacy in Cloud Computing and IoT.
- More Posts(3)
![]() Techniques for assessing privacy and data protection in software systems por dsguaman está licenciado bajo una Licencia Creative Commons Atribución-NoComercial-SinDerivar 4.0 Internacional.
Techniques for assessing privacy and data protection in software systems por dsguaman está licenciado bajo una Licencia Creative Commons Atribución-NoComercial-SinDerivar 4.0 Internacional.

