Towards the application of privacy patterns
This note is a summary of the paper “A framework and roadmap for enhancing the application of privacy design patterns” [1].
Privacy patterns have gained a lot of attention to the realization of the Privacy by Design paradigm and the development of privacy-friendly information systems [2][3]. Despite of being not mature enough, they and proposals based on them (e.g. [4][5]) are part of guidelines provided by European agencies of cybersecurity (European Union Agency for Cybersecurity -ENISA [6], Spanish Data Protection Authority [7]).
Privacy patterns, based on the design pattern concept [8], are design solutions to recurring problems in a privacy context. For example, in situations where the identity needs to be protected from exposure, it is possible to use the pattern Pseudonymous Identity [9], which uses a random pseudonym instead of the original identity. Privacy patterns aim to be easily read, understood and applied [10].
Such versatility has made privacy pattern based contributions the most reported for the design of privacy-friendly systems [11]. However, they have mainly focused on the development of new patterns, their evolution to pattern languages and on methodologies including them, lacking studies into the factors influencing the application of privacy patterns. The application process is far from trivial, and overlooking this could hinder their adoption and the success of proposals based on them.
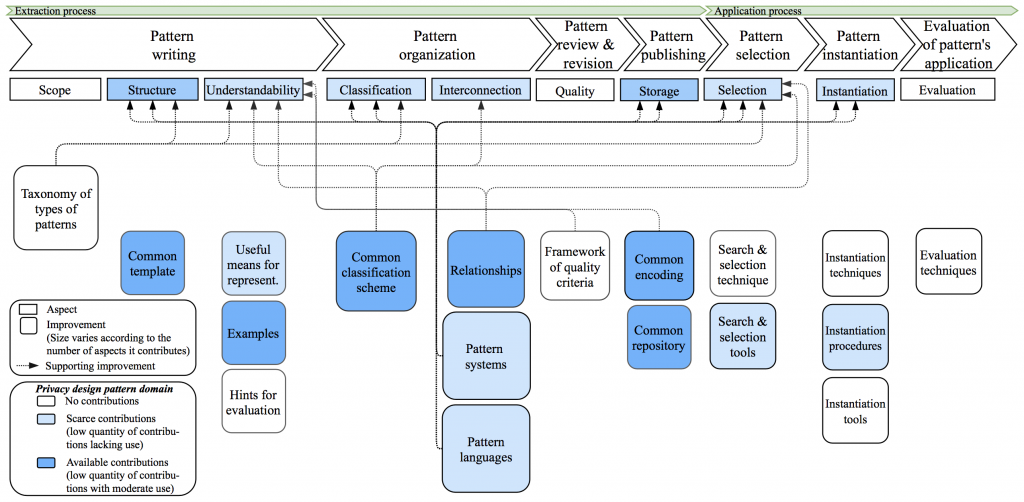
The application process has already been approached in the more mature and very close domain of security patterns [12] [13]. Studying that domain has made it possible to propose a framework to describe the application process in detail (Fig. 1). The framework contains the aspects influencing the application of a pattern, which are organized according to the activities of the pattern lifecycle [14]. Within each aspect, there may be drawbacks (negatively) and solutions (positively) affecting the application process.
As there have been some proposals that might contribute to easing the application of privacy patterns, we show them in the framework (Fig. 1) as solutions existent in the state of the art of the privacy pattern domain. Thus, it is possible to see in which aspects more solutions are still required. These are necessary to foster a future adoption of privacy patterns and all the increasing privacy engineering methods, techniques and tools based on them.
The most promising research lines include elaborating a taxonomy of types of patterns, including useful means for representation when writing patterns, proposing more pattern systems and languages, and developing instantiation techniques and supporting tools.
Key concepts:
- The application process is carried out by a developer and includes: the identification of a problem and context where a pattern could be instantiated, the selection of a pattern, its instantiation and the evaluation of the instantiation.
- The instantiation of a pattern is a stage where the developer uses/applies the pattern’s solution to solve a given problem (or task).
- An application aspect is a category that includes elements affecting positively (solutions) or negatively (drawbacks) the successful instantiation of a pattern.
- The application framework includes all the application aspects organized according to the stages of the pattern lifecycle.
References
[1] Caiza, J. C., Del Alamo, J. M., & Guamán, D. S. (2020). A framework and roadmap for enhancing the application of privacy design patterns. The 35th ACM/SIGAPP Symposium On Applied Computing, 1297–1304. https://doi.org/10.1145/3341105.3375768
[2] Hazeyama, A. et al. 2017. Literature survey on technologies for developing privacy-aware software. 2016 IEEE 24th International Requirements Engineering Conference Workshops (REW) (Beijing, China, Sep. 2017), 86–91.
[3] Lenhard, J. et al. 2017. A literature study on privacy patterns research. Proceedings – 43rd Euromicro Conference on Software Engineering and Advanced Applications, SEAA 2017 (Vienna, Austria, 2017), 194–201.
[4] Notario, N., Crespo, A., Martin, Y. S., Del Alamo, J. M., Metayer, D. Le, Antignac, T., Kung, A., Kroener, I., & Wright, D. (2015). PRIPARE: Integrating privacy best practices into a privacy engineering methodology. 2015 IEEE Security and Privacy Workshops, 151–158. https://doi.org/10.1109/SPW.2015.22
[5] Hoepman, J.-H. (2014). Privacy design strategies. In N. Cuppens-Boulahia, F. Cuppens, S. Jajodia, A. Abou El Kalam, & T. Sans (Eds.), ICT Systems Security and Privacy Protection. SEC 2014. IFIP Advances in Information and Communication Technology (Vol. 428, pp. 446–459). Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-642-55415-5_38
[6] Danezis, G., Domingo-Ferrer, J., Hansen, M., Hoepman, J.-H., Metayer, D. Le, Tirtea, R., & Schiffner, S. (2014). Privacy and Data Protection by Design – from policy to engineering (Issue December). European Union Agency for Cybersecurity. https://doi.org/10.2824/38623
[7] Spanish Data Protection Authority. (2019). A Guide to Privacy by Design.
[8] Gamma, E. et al. 1995. Design Patterns: Elements of Reusable Object-Oriented Software. Addison-Wesley
[9] Hafiz, M. (2013). A pattern language for developing privacy enhancing technologies. Software – Practice and Experience, 43(7), 769–787. https://doi.org/10.1002/spe.1131
[10] Meszaros, G. and Doble, J. 1998. A pattern language for pattern writing. Pattern languages of program design. (1998).
[11] Caiza, J.C. et al. 2019. Reusable Elements for the Systematic Design of Privacy-Friendly Information Systems: A Mapping Study. IEEE Access. (2019), 1–1.
DOI:https://doi.org/10.1109/ACCESS.2019.2918003.
[12] Ito, Y. et al. 2015. Systematic Mapping of Security Patterns Research. Proceeding PLoP ’15 Proceedings of the 22nd Conference on Pattern Languages of Programs (2015), 3–4.
[13] Washizaki, H. 2017. Security patterns: Research direction, metamodel, application and verification. 2017 International Workshop on Big Data and Information Security (IWBIS) (Sep. 2017), 1–4.
[14] Elshaafi, H. et al. 2015. PRIPARE: Guidelines for Best Practice Templates.
About Julio César Caiza
Starting in the world of Privacy Research. PhD student at Universidad Politécnica de Madrid (SPAIN). Auxiliary Professor at Escuela Politécnica Nacional (ECUADOR).
- Web |
- More Posts(4)
![]() Towards the application of privacy patterns por jcaiza está licenciado bajo una Licencia Creative Commons Atribución-NoComercial-SinDerivar 4.0 Internacional.
Towards the application of privacy patterns por jcaiza está licenciado bajo una Licencia Creative Commons Atribución-NoComercial-SinDerivar 4.0 Internacional.

