Bypassing Certificate Pinning in Android Applications
There are more and more applications available on our mobile phones that make our lives a little easier or even more entertaining at certain times. However, it is true that these applications can make use of (and abuse) data that is generated or gathered by the terminals, such as, for example, GPS positioning, camera, contacts, among others, and send them to remote servers. In order to better understand what these apps are doing with our data we need to be able to audit their communications, even if they are encrypted.
This post briefly describes a security technique called Certificate Pinning, which is used by Android apps to protect their communications against basic Man in the Middle attacks. We have developed advanced mechanisms that facilitate auditing encrypted traffic in a laboratory environment, even when they are protected by Certificate Pinning[1].
Certificate pinning
Certificate pinning refers to the process by which a client application gets a reference to the certificate to be used to stablish an SSL connection, and checks it when setting up the connection to avoid Man in the Middle attacks. In the case of Android, applications may include a copy of a certificate in such a way that this anchored certificate is compared with the server certificate when setting a secure connection
The figure below shows the steps for setting certificates in the SSL / TLS communications security protocol. The client verifies the certificate that the server has just sent. The client is able to verify the validity of the certificate using a fixed key or fingerprint of the certificate.
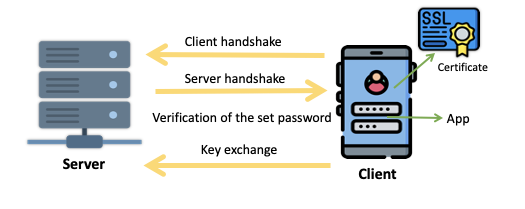
Bypassing certificate pinning
A Man in the Middle (MitM) attack consists on an attacker being able to place himself between the communication of two entities so that he can intercept, read and modify all the traffic that is being generated. Basically, the attacker is “in the middle” of the communication and deceives the two parties by posing as each of them when they are communicating.
MitM attacks fail to deceive applications protected by certificate pinning methods, since the client is able to check the server certificate and detect whether it has been replaced. To this end, applications usually rely on specific libraries that manage the underlying checks.
We have used dynamic instrumentation techniques to inject code to the client applications overcoming the certificate pinning checks, thus being able to carry out the MitM attack and observe the ongoing communications.
To this end we have used the Frida dynamic instrumentation tool. The modified code is built taking into account the classes and methods of the libraries that Android applications use to implement certificate pinning. Tests were carried out to install, execute and test nearly a thousand applications from Google Play. The following table provides an overview of the results. For further details, the interested reader can check Andrea del Nido’s Master Thesis entitled “Development of mechanisms for traffic auditing of Android applications”.

[1] Andrea del Nido García has received a MSc on Cybersecurity at Universidad Politécnica de Madrid. She elaborated a Master’s Thesis entitled “Development of mechanisms for traffic auditing of Android applications” under the supervision of Jose M. del Alamo.
About Jose M. Del Alamo
![]() Bypassing Certificate Pinning in Android Applications por jmdelalamo está licenciado bajo una Licencia Creative Commons Atribución-NoComercial-SinDerivar 4.0 Internacional.
Bypassing Certificate Pinning in Android Applications por jmdelalamo está licenciado bajo una Licencia Creative Commons Atribución-NoComercial-SinDerivar 4.0 Internacional.
