Cybersecurity
Existing Information Technology (IT) systems constantly expose their assets (information, processing systems or computational resources) to public exposition, because of Internet mainly, entailing potential threats on such assets. This fact can clearly open our vision to focus the attention on how to adequately protect assets for mitigating potential threats and their impact. In addition, other organization assets are often underestimated but equally dangerous: its human resources, such as employees of the organization who have first-hand access to critical assets that can lead to leakage information. Remote accesses and the use of mobile devices at the workplace (BYOD policies) are increasingly being granted by organizations to allow employees interacting with operational assets, thus increasing the risk over them.
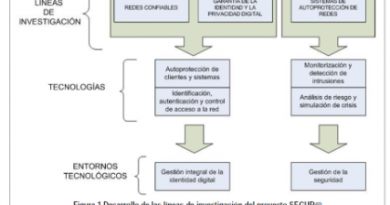
Cybersecurity can be seen as the set of processes, policies and technologies deployed by an organization in order to protect its assets. Research on cybersecurity can be approached from different perspectives, each of them rolling out specific research lines.
Research on Threats and Vulnerabilities
Knowing your enemy is more than an ancient saying. It is an urgent necessity to understand the needs of security services to deploy in an organization. Current research lines of the groups in this area include:
-
Threat detection, by anomalies detection and application of Machine Learning technologies to this area
-
Threat prevention, detecting symptoms that can lead to potential attacks. This can be addressed from different perspectives:
-
Analysis of context parameter deviations (e.g. traffic profiling, systems context, network context)
-
Application of Machine learning technologies for prevention: detection of multi-step attacks
-
From a human point of view, by detecting potential factors in employees that can evolve to an internal employee attack
-
-
Vulnerabilities detection, with application of different audit methodologies to specific devices in order to identify potential weakness.
Research on Cybersecurity Services
The design, development, deployment and integration of cybersecurity services is already a mature area, but there are some research gaps that can improve and optimize the application of these services to different environments. These research lines are:
-
Federated Authentication mechanisms, integrating access control of all the systems, services and devices in an organization.
-
Network security, addressing the protection of communications in different scenarios, such as IMS and SIP Protocol, IoT communications, 5G mobile networks, etc.
Research on Cybersecurity Operation and Management
Running effectively a cybersecurity centre is one the most demanded capacities in the organizations. The market situation is not as mature as with the cybersecurity technologies, and there are different areas where research can play a key role for evolving the current state of the art. The current research lines of the group in this area include:
-
Automatic Response Intrusion Systems: the research will help to define metrics in order to identify the most appropriate response for a given attack, taking into account as much information as possible for taking that decision: context of the intrusion, target assets, response costs, etc.
-
Deception responses: deployment of ad-hoc honeynets for a given attack, optimized for the characteristics of an attack, in order to integrate them as a possible response in an Automatic Response Intrusion System
-
Dynamic Risk Assessment: In this area, the research tries to develop a new framework, which allows a continuous risk assessment process, taking into account security from a holistic approach. Risks will be modified taking into account any potential input, being it from the traditional ICT Security Infrastructures or from any other source and dynamically modifying the risk level of the organization. An effective Threat Intelligence integration will play a key role in this area, as well as the formal definition of security metrics for the dynamic risk definition.
-
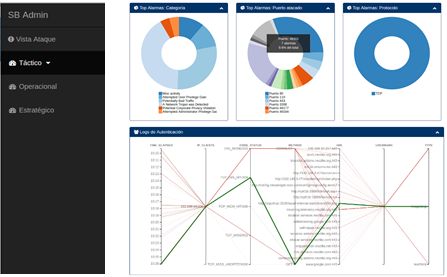
Situational Awareness: Because of an effective dynamic risk assessment, and the integration of different research areas, such as threat detection and prevention, it is possible to provide an optimized situational awareness functionality for different organization teams (operators, analysts, managers, etc.)
Research on Cybersecurity Education
Training and awareness in cybersecurity is the last, but not least, component of the area. In this area research will help to define effective training technologies and processes optimized for different educational goals, from basic cybersecurity knowledge oriented towards non technical society areas, like children, families, etc. to specialized cybsercecurity simulation scenarios for technical analysts and operator. The group is working currently in these research lines:
-
Guides of cybersecurity awareness for children and families: processes, tools, etc. for increasing the cybersecurity knowledge and awareness for that part of the civil society
-
Cybersecurity Technological Simulation Platforms, for the training of technical operator and analysts, able to host different cybersecurity experiments for a large number of trainees.